Microsoft Defender Vulnerability Management
Reduce cybersecurity threats with a risk-based approach to vulnerability management.

Expansion of Defender Vulnerability Management
Defender Vulnerability Management is now available as a standalone offer for more customers and use cases. It complements your endpoint detection and response (EDR) solution and has been expanded to include vulnerability assessments of containers.
Risk-based vulnerability management
Reduce risk with continuous vulnerability assessment, risk-based prioritization, and remediation.
Continuously discover and monitor assets
Eliminate periodic scans with continuous monitoring and alerts. Detect risks even when endpoints are not connected to the corporate network.
Focus on what matters
Prioritize the biggest vulnerabilities on your most critical assets using Microsoft threat intelligence, breach likelihood predictions, and business contexts.
Track and mitigate risks with ease
Bridge the gap between security and IT teams to seamlessly remediate vulnerabilities with robust contextual recommendations, built-in workflows, and application block capabilities to enable protection faster.
Get comprehensive coverage
Use agent-based or agentless scans across cloud workloads, servers, containers, and endpoints with support for Windows, Linux, macOS, iOS, and Android.
Get ahead of cyberthreats
Continuously discover, prioritize, and remediate the biggest risks to organizations across endpoints and cloud workloads.
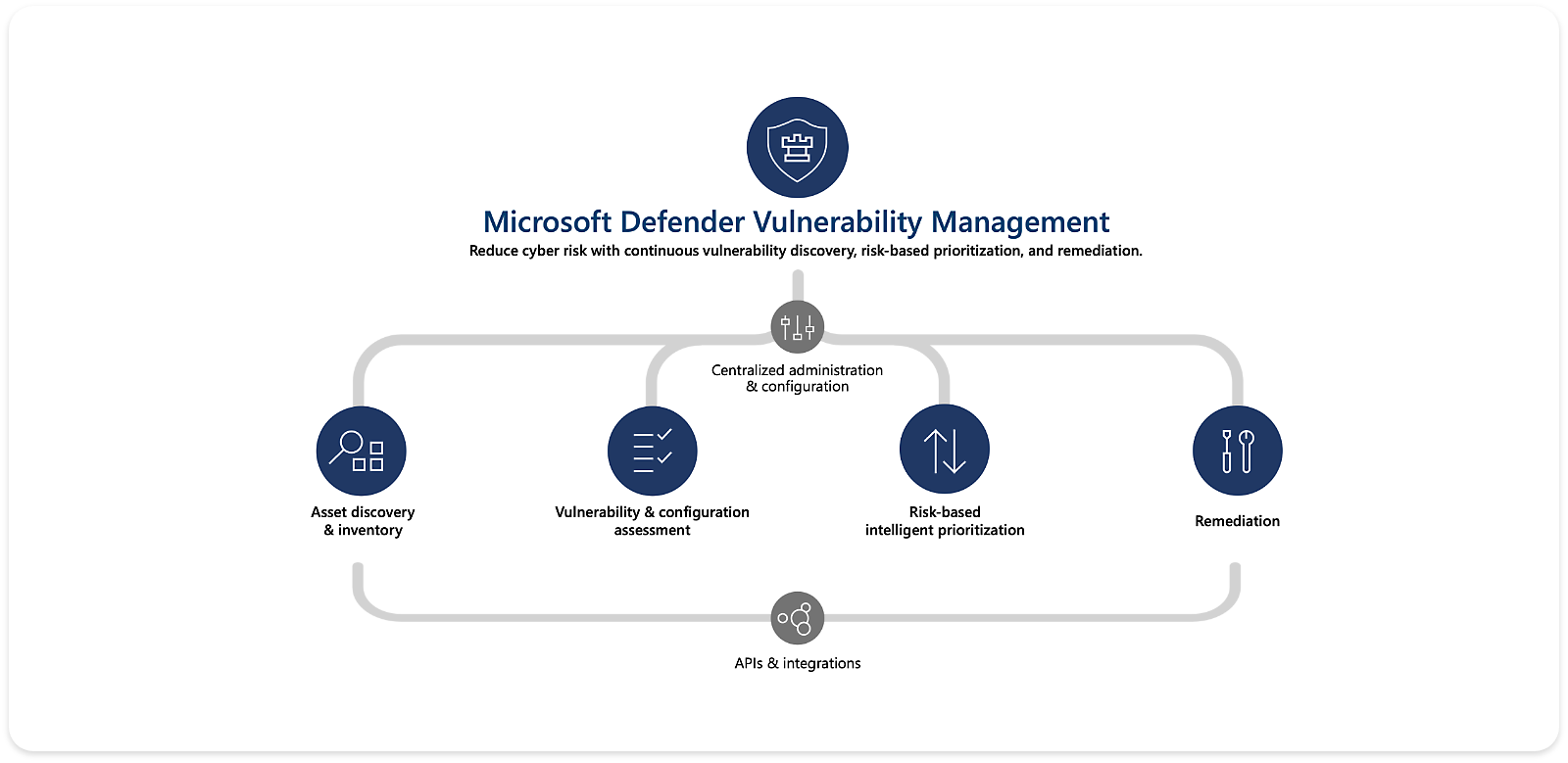
Key capabilities
Proactively reduce risk to your organization with Defender Vulnerability Management.

Discover vulnerabilities in real time
Detect risks across managed and unmanaged endpoints with built-in modules and agentless scanners, even when devices aren’t connected to the corporate network.

Reduce risk with continuous assessments
Eliminate periodic scans and access entity-level inventories of devices, software applications, digital certificates, browser extensions, and firmware assessments.

View prioritized security recommendations
Focus on cyberthreats that pose the highest risk with a single view of prioritized recommendations from multiple security feeds.

Block vulnerable applications
Proactively block known vulnerable versions of apps or warn users with customized desktop alerts.

Seamlessly remediate and track progress
Connect teams with built-in workflows and integrations. Track progress and trends in real time with remediation tracking and device reports.

Vulnerability assessments across cloud workloads
Get agentless and agent-based vulnerability scanning for agility and comprehensive workload protection.
Unified security operations platform
Secure your digital estate with the only security operations (SecOps) platform that unifies the full capabilities of extended detection and response (XDR) and security information and event management (SIEM).
Unified portal
Detect and disrupt cyberthreats in near-real time and streamline investigation and response.
Defender XDR
Achieve unified security and visibility across your clouds, platforms, and endpoints.
Microsoft Sentinel
Aggregate security data and correlate alerts from virtually any source with cloud-native SIEM.
Get started
Get proactive protection across different domains including endpoints, servers, and cloud workloads with Defender Vulnerability Management.
Vulnerability management plans
- For Microsoft Defender for Endpoint Plan 2 customers: Seamlessly enhance your vulnerability management program—without the need for additional agents—using the Defender Vulnerability Management add-on.
- For Microsoft Defender for Cloud customers: Get agentless vulnerability management for servers, containers, and container registries with Defender Vulnerability Management—natively integrated within Defender for Cloud.
- For other customers: Complement your existing EDR solution with the Defender Vulnerability Management standalone offering.
Related products
Use best-in-class Microsoft security products to help prevent and detect cyberattacks.

Microsoft Defender for Endpoint
Get leading endpoint security to rapidly stop cyberattacks and scale your security resources.

Microsoft Secure Score
Gain visibility, insights, and intelligent guidance to strengthen your security posture.

Microsoft Defender for Cloud
Detect and respond to cyberthreats in real time to help protect your multicloud, hybrid, and on-premises workloads.

Microsoft Defender Threat Intelligence
Help protect your organization from modern adversaries and cyberthreats such as ransomware.
Documentation and latest updates
Documentation
Learn about each capability in depth and how it can help you protect your organization.
Download the solution brief
Explore how Defender Vulnerability Management helps discover, assess, and remediate risk.
Latest updates
Learn about the latest innovations in vulnerability management from Microsoft.
Protect everything
Make your future more secure. Explore your security options today.





Follow Microsoft Security