Azure Active Directory (Azure AD) is now Microsoft Entra ID.
Microsoft Entra conditional access
Increase protection without compromising productivity.

Reimagine secure access with Microsoft Entra
Discover the latest identity and access innovations and how to strengthen your defenses with Microsoft Entra.
What is conditional access?
Conditional access is an intelligent policy engine that helps organizations better control how users access corporate resources.
Enforce access controls with adaptive policies
Bring together real-time signals such as user context, device, location, and session risk information to determine when to allow, block, or limit access, or require additional verification steps.
Help protect data inside applications
Monitor and control sessions, application access, and sensitive data across your organization in real time based on user behavior in apps, both on premises and in the cloud.
Restrict access for vulnerable and compromised devices
Use conditional access policies to check the device health and security posture of registered devices and ensure only healthy and trusted devices can access your corporate resources.
Learn more about conditional access concepts
How conditional access works
Conditional access takes in over 40 TB of identity-related security signals and analyzes them using machine learning to determine the appropriate policy to apply to a resource.
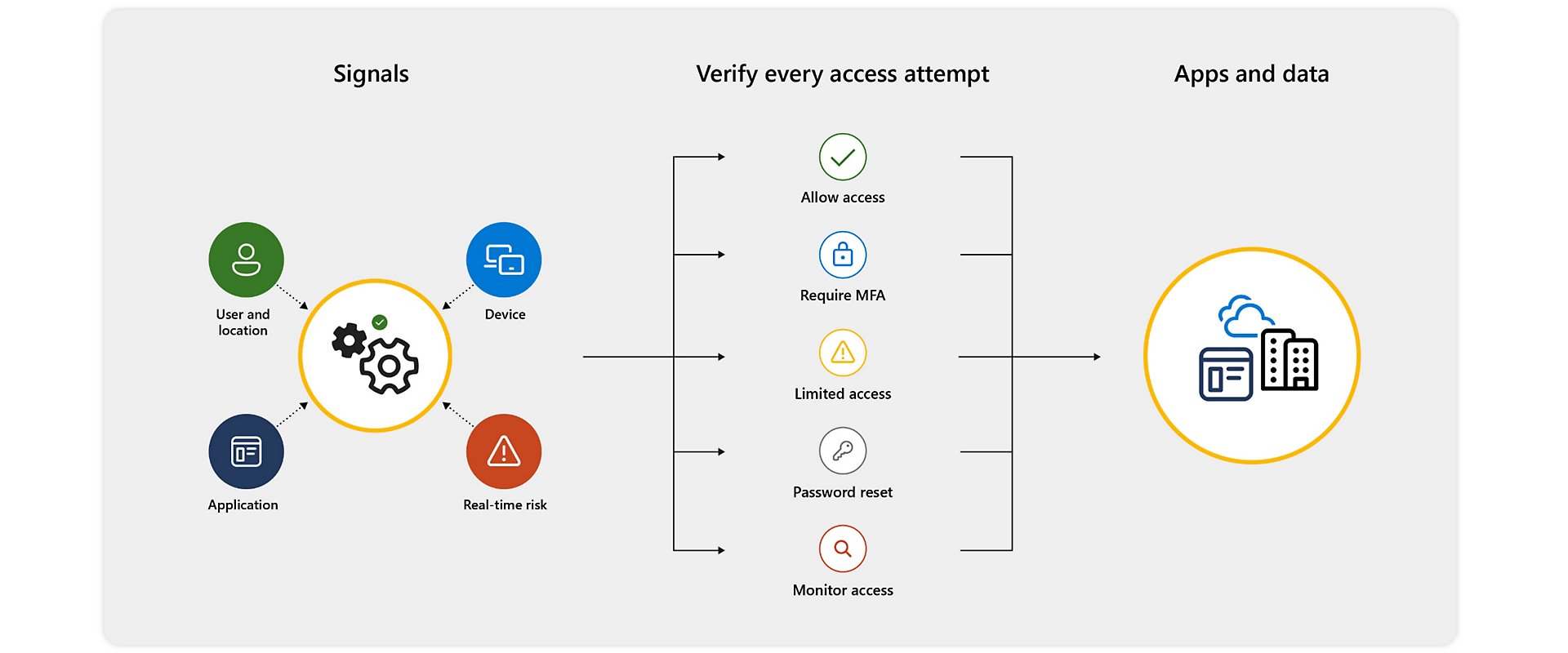
Microsoft Entra conditional access capabilities

Build adaptive access polices
Manage security controls with custom-built conditions to block access, require multifactor authentication, or restrict a user’s session only when needed.
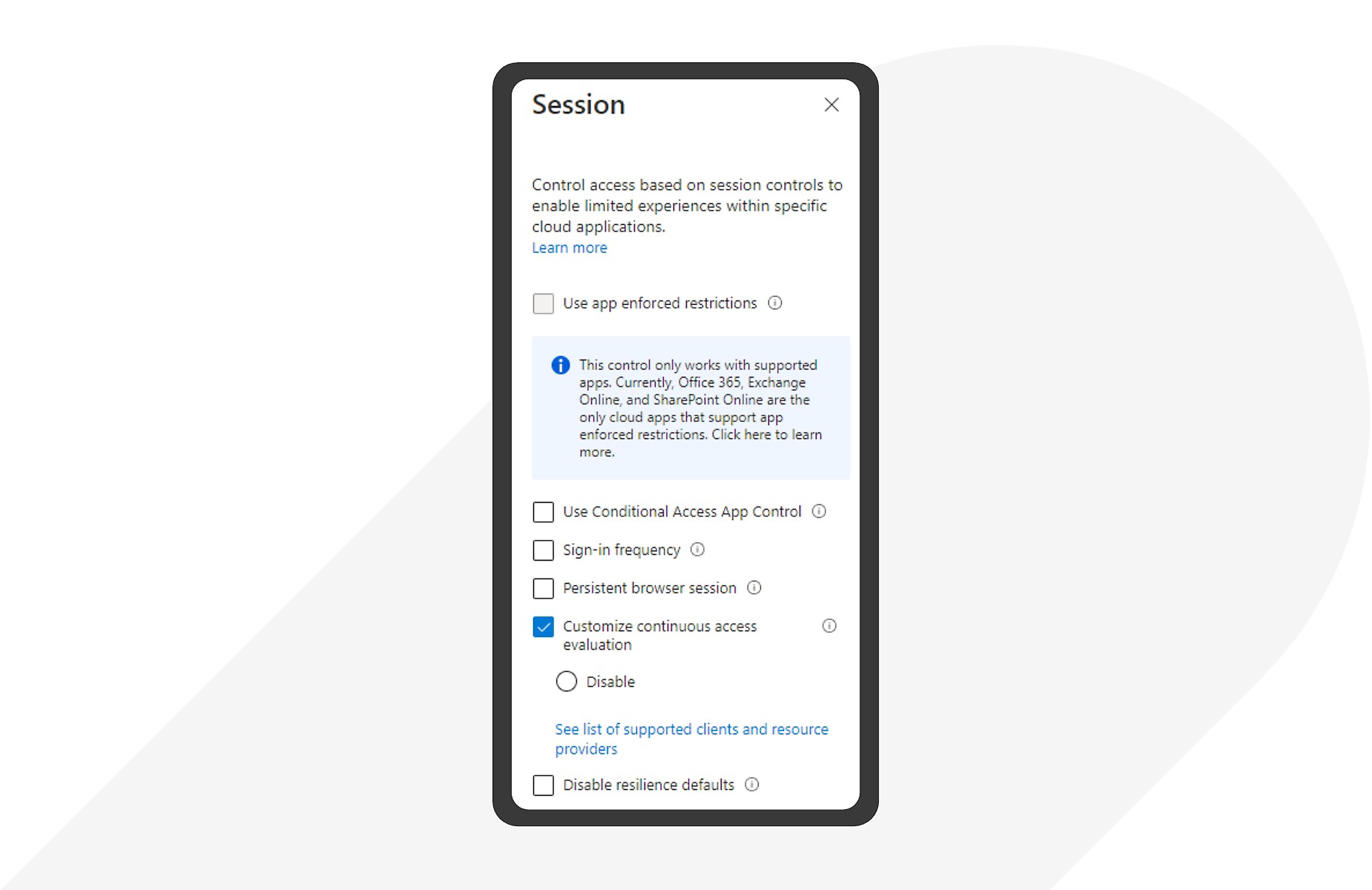
Monitor access and enforce policies in session
Help ensure post-authentication protection with in-session monitoring and access-control policies.
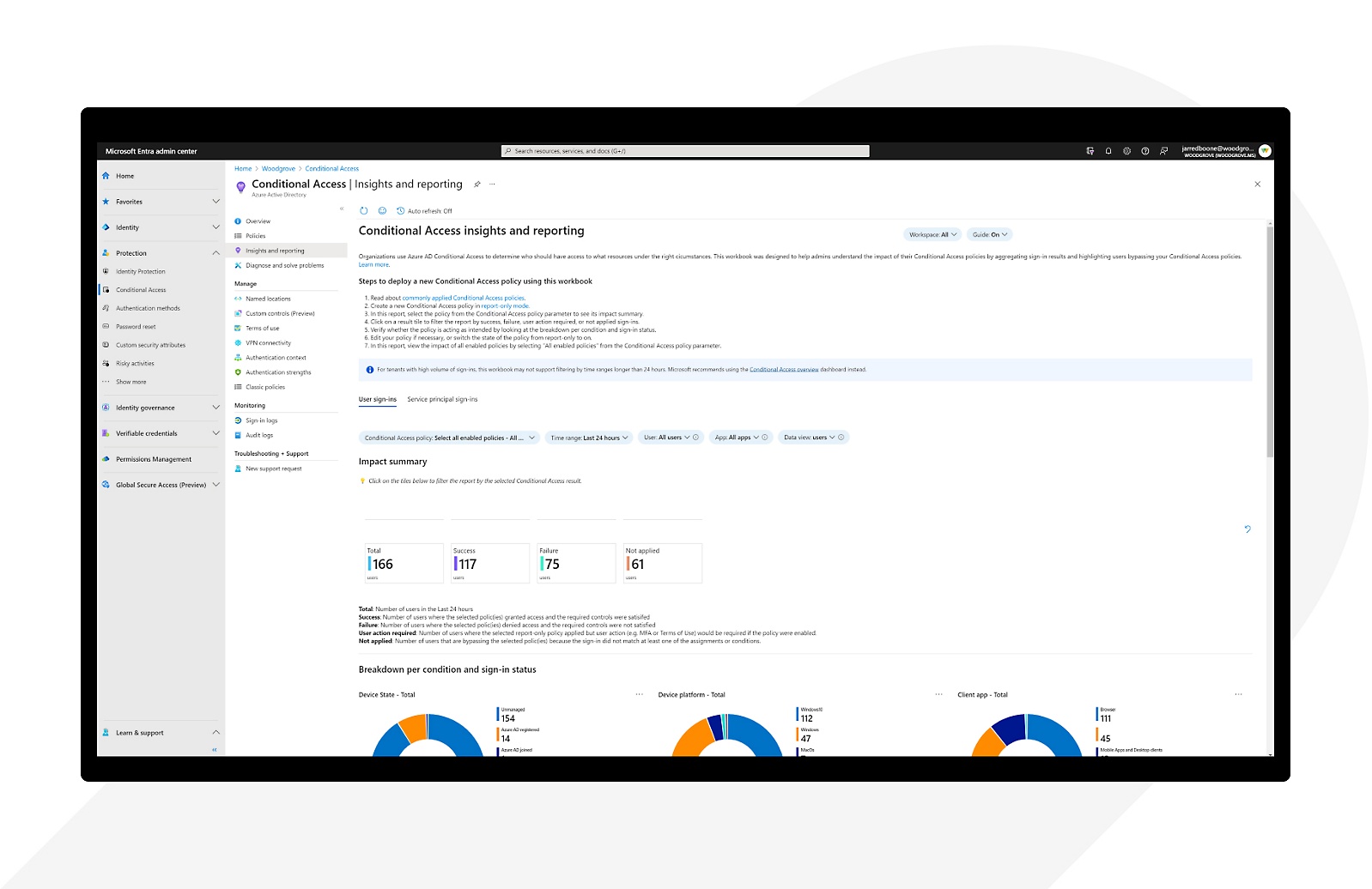
View in report-only mode
Use report-only mode to monitor the impact of policies before enforcement to fine-tune access policies before rollout.
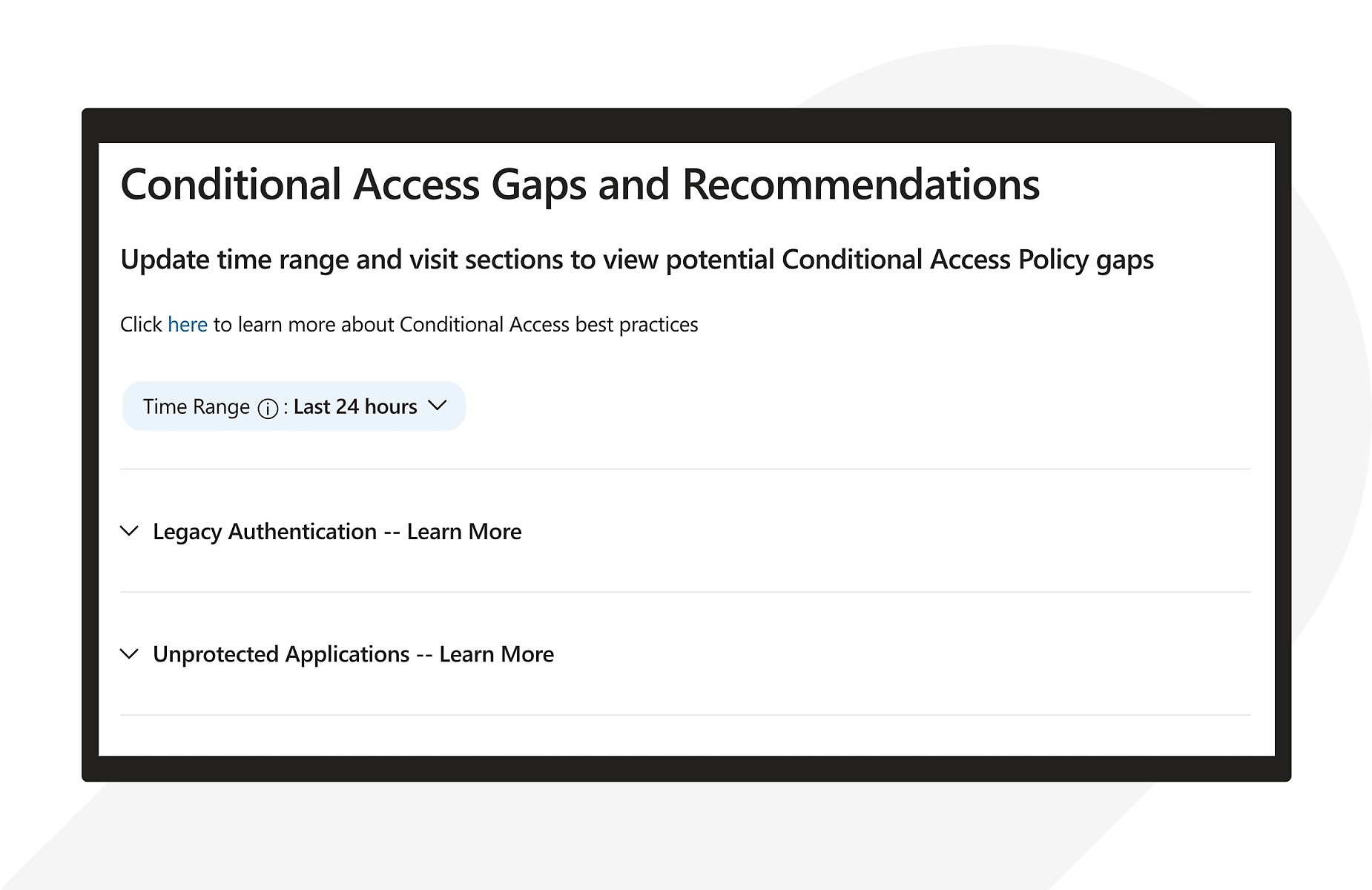
Fine-tune access policies with actionable guidance
Get a security report that identifies opportunities for improvement and provides recommendations.
See why more than 300,000 organizations use Microsoft Entra ID
Microsoft Entra ID pricing
Conditional access capabilities are available with a Microsoft Entra ID P2 subscription
- Azure Active Directory P2 is now Microsoft Entra ID P2.
- Microsoft Entra ID P2 is included with Microsoft 365 E5, including versions of this suite that do not include Microsoft Teams, and offers a free 30-day trial.
- Azure and Microsoft 365 subscribers can buy Microsoft Entra ID P2 online.
Documentation and training
Protect everything
Make your future more secure. Explore your security options today.


Follow Microsoft Security