Global threat activity
Countries or regions with the most malware encounters in the last 30 days
Living off the land: Attacks that barely touch the disk

Running code with system tools
Sophisticated attacks avoid dropping files and instead rely on system tools to run malicious code directly from remote or hidden sources. The absence of files leaves AV scanners without the necessary triggers and forensics without persistent artifacts to recover. While security solutions have evolved, many don’t check memory or review behaviors at runtime. Some rely on static approaches that don’t dynamically recognize new attack methods.
Read about fileless attacks and defenses
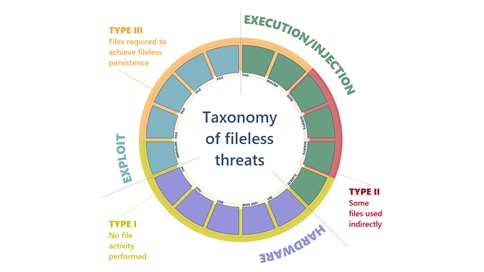
Fileless in more ways than one
Attacks can go fileless in many ways. Attackers often use scripts, but they also attempt to inject code into memory, hijack COM objects, and even insert malicious code into firmware. Although these fileless techniques have figured in targeted attacks, they have become more common in commodity malware campaigns.
Learn about fileless techniques
Protect with Microsoft Defender for Endpoint
Microsoft Defender for Endpoint provides several layers of defenses, including next-generation antivirus protection powered by behavior monitoring and runtime script analysis. Both AV and EDR sensors use machine learning algorithms that actively learn from both static and behavioral data to identify new fileless attacks.
Most affected industries
Reported enterprise malware encounters in the last 30 days






