Secure research starts with responsible testing.
Microsoft Researcher Recognition Program
Partner with Microsoft to strengthen our products and services by identifying and reporting security vulnerabilities that could impact our customers.
The Microsoft Researcher Recognition Program offers public thanks and recognition to security researchers who help protect our customers through discovering and sharing security vulnerabilities under Coordinated Vulnerability Disclosure.
Anyone who submits a security vulnerability to the Microsoft Security Response Center (MSRC) is eligible to participate.
To view our leaderboards, please visit the MSRC Leaderboard site.
Is this your first time reporting to the MSRC? Want to learn more about our case process? Visit our MSRC Researcher Resource Center to watch the Researcher Onboarding Video to learn about the Rules of Engagement, case process, available rewards through the Bounty Program, recognition leaderboards, and our disclosure process.
Bounty Leaderboard Launching July 2026
Starting in July 2026, MSRC will replace the points-based leaderboards with bounty-based leaderboards.
To learn more, read the MSRC announcement.
Program Overview
Points-based leaderboards will continue to acknowledge researchers on a quarterly basis through June 30, 2026. However, there will be no points-based Most Valuable Researcher (MVR) list published this year. Researchers will be recognized on this year’s MVR Bounty Leaderboard based on the total amount of bounty rewards they earn from July 1, 2025, through June 30, 2026.
We award researchers points for each valid submission to the MSRC, and accumulated points earn researchers recognition on Microsoft’s Quarterly, Annual, and Technical Leaderboards, with the Top 100 from the Annual Leaderboard gaining the title of Most Valuable Researcher (MVR). MVRs may receive profile badges and swag for achievements in high impact, high accuracy research, and volume for their research.
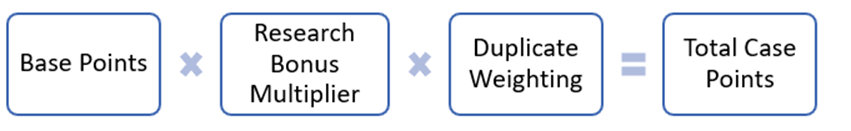
How do points work?
It works like this:
Base Points
We award researchers points for each valid vulnerability reported to the MSRC. Base points are determined by the severity and security impact of each vulnerability submitted.
| Vulnerability Type | Critical | Important | Moderate | Low | None |
|---|---|---|---|---|---|
| Remote Code Execution | 60 | 40 | 0 | 0 | 0 |
| Elevation of Privilege | 40 | 20 | 0 | 0 | 0 |
| Information Disclosure | 30 | 15 | 0 | 0 | 0 |
| Spoofing | 20 | 15 | 0 | 0 | 0 |
| Security Feature Bypass | 0 | 10 | 0 | 0 | 0 |
| Tampering | 0 | 10 | 0 | 0 | 0 |
| Denial of Service | 0 | 5 | 0 | 0 | 0 |
Research Bonus Multipliers
We award additional bonus points for vulnerabilities found in certain high-impact products and services. This list is subject to change over time, so keep an eye on the research bonus multipliers list!
| Multiplier | Products and Services |
|---|---|
| 3X Research Areas | Azure (including but not limited to Azure Services such as Azure Portal, Cloud Shell, Cloud Service, Azure Kubernetes Service, Azure Functions, Key Vault, Azure DevOps) Identity Windows (Hyper-V and eligible attack scenarios) |
| 2X Research Areas | Exchange Online Teams Dynamics 365 Windows Defender Edge on Chromium MSRC Portal IoT AI/ML |
| 1X Research Areas | All other research areas not included in the 3X, 2X, or Out of Scope list |
| Out of Scope Research Areas | Subdomain Takeover Vulnerabilities GitHub* LinkedIn* End of Support Products |
*Microsoft Security Response Center does not currently service vulnerabilities in GitHub or LinkedIn. To report an issue, go to GitHub's Bug Bounty Program and LinkedIn's Bug Bounty Program.
Duplicate Weighting
What if I report a vulnerability someone else already reported?
If you are the first person to submit a report for an unpatched vulnerability, you receive 100% of the points.
If you are the second to submit a report, you receive 50% of the points.
Additional reports of the same issue receive no points.
Leaderboards
Case points will be awarded based on Assessment Date time stamp to ensure that cases that span two recognition periods are not missed.
Each quarter, cases assessed within that quarter will recieve points.
Quarterly Leaderboard
Each quarter, we recognize all researchers who have received more than 20 points. In addition, we recognize researchers in specific research and technology areas in our Technical Leaderboards. Quarterly Technical Leaderboards recognize research in Azure, Office, Windows, and Dynamics.
Annual Leaderboard
Each year we recognize the MSRC's Most Valuable Researchers who have achieved the Top 100 ranks.
Each program period runs from July 1 to June 30. For example, the 2025/2026 program period runs from July 1, 2025, to June 30, 2026.
Annual leaderboards include technical leaderboards for Azure, Office, Windows, and Dynamics. Researchers who do not make the MVR top 100 are eligible for quarterly leaderboards and will receive accuracy, impact, and volume badges where applicable on the published leaderboard page, but will not receive a digital form of the badge.
Technical Leaderboard
Technical Leaderboards recognize researchers who have distinguished themselves through high-impact research in specific areas, including Azure, Office, Windows, and Dynamics. Technical leaderboards publish the top 10 ranks for each technical group for both Quarterly and Annual Leaderboards.
Annual Technical Leaderboards are not limited to the Top 100 and will feature all the Top 10 researchers each technical group regardless of MVR status.
Most Valuable Researcher
The top 100 researchers from the Annual Leaderboard will receive the title of Most Valuable Researcher and will receive digital badges.
Digital Badges
Digital badges highlight researchers’ accomplishments throughout a program period and can be shared on professional profiles and social media such as LinkedIn and Twitter. The first badge recognizes our 2020 Most Valuable Security Researchers, with more badges to come!
Accuracy Badge: Recognizes researchers with 100% accuracy, meaning all their submissions were valid vulnerability reports
Impact Badge: Recognizes high-impact work, with the average points per valid vulnerability report at or above the 90th percentile
Volume Badge: Recognizes a larger body of work, requiring at least five valid vulnerability reports
Swag
Researchers who earn a position on the quarterly leaderboards will receive a claim link to select swag from options list on SwagMagic.
Each year, a specifically designed SWAG box is sent to Microsoft’s Most Valuable Security Researchers (MVRs). This generally happens in the Fall after the annual MVR announcement, and each researcher eligible for a Swag box will be notified by our team.
How to set your Leaderboard Name or choose to be displayed as Anonymous
For all researchers, if you’d like to have your name included in ongoing Quarterly and Annual leaderboards, please confirm or update your “Preferred Name” in the Researcher Portal. Preferred names cannot be changed once published.
You can update your Preferred Name and change your Recognition Preference anytime by logging into your MSRC Researcher Portal account. Note, both fields must be filled out to be opted-in for recognition.
- Select your Recognition Program Preference
We periodically recognize our top performing researchers on publicly available web pages (e.g. leaderboards). Researcher recognition programs are always “opt-in”, by default you are anonymous, but you may choose to be recognized by name or alias. You can indicate your recognition preference by selecting one of the options below in your MSRC Researcher Portal profile:
- Opt-in to the researcher recognition program, display my name as Anonymous
- Opt-in to the researcher recognition program, display my Preferred Name
- Opt-out from the researcher recognition program
- Provide your Preferred Name for Recognition
If you selected to display your Preferred Name for leaderboard recognition, you can click “Edit” to update your Preferred Name
Additional Information
Check out the frequently asked questions (FAQs). Still have questions? Email us at msrcmvr@microsoft.com.
Revision History
- July 29, 2019: Information Published
- 2019-2025: Points-based Leaderboards published
- February 6, 2026: Bounty Leaderboard Announcement
